
Keyless Entry technology, like the one installed in Tesla vehicles, is designed to make it easier for you to get into your car without having to fumble with keys. You can just walk next to the car, and the car will unlock. However, this technology also makes it easier for thieves to get in your car if they know what they’re doing. Despite some technological improvements in Tesla’s vehicle technologies, security researchers have found it’s still possible to steal Teslas.
Here’s how the technology works: the Tesla and the key fob are always talking to each other. The key fob sends a signal to the Tesla, and if the Tesla detects the key nearby, it unlocks and starts. But how does the car really knows that you are near? it typically uses the strength of the signal being received. And this is where the problems begin.
For Tesla users, the smartphone is used to allow them to open the car.
In the past thieves have used devices called relay boxes to extend the reach of this signal. One thief stands near the Tesla with a relay box that picks up the car’s signal. Another thief stands near your house with another relay box that captures the signal from your key fob. The two relay boxes talk to each other and pass the data, using high powered transmitters, to make the Tesla think the key fob is right next to it, even if it’s inside your house. This way, the thieves can unlock your car, start it, and drive away without needing the actual key.
This method of car theft is becoming more common because it’s quick and doesn’t require breaking into the car or using force.
In the last few years, car companies including Tesla have added a new type of radio called Ultra-wideband communications into some vehicles like the Tesla Model 3. This technology allows for more accurately locating devices, and it was expected that it would help prevent these kind of attacks. The same technology is used for example in Apple AirTags to accurately find devices.
Unfortunately, an investigation from an automotive security firm GoGoByte has shown that the latest Tesla Model 3, one of the most popular models, is still vulnerable to relay attacks even though it has ultra-wideband.
Understanding Wireless Relay Attacks
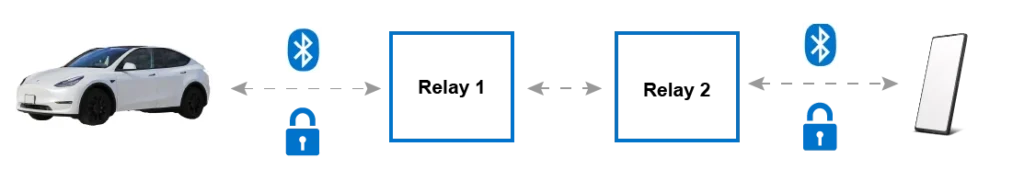
When car thieves are performing a wireless relay attack, they’re using two devices that each capture the signals that a car uses to authenticate and get the range. Because the two devices just capture and forward the data, the car and smartphone or keyfob believe the other device is nearby.
Relaying Packets
As you can see above, the two relay devices sit next to the respective devices. Relay 1 is near the car, and Relay 2 will be placed by thieves near the keyfob or smartphone. Thieves have been known to get close to bedrooms where people will typically have their keys or other similar locations.
The two relays will communicate using some wireless protocol. This is typically low latency and with high power to overcome long distances. Each devices captures packets being sent by the keyfob/smartphone and/or car and retransmit any packet they receive belonging to the device. They don’t have to filter – they can essentially retransmit any packet they see.
In the case of Tesla, both the Tesla Model 3 and Model Y use Bluetooth Low Energy (BLE) to implement the keyless entry system. When the smartphone or keyfob are nearby, it allows the car to unlock and even drive. Back in the old days thieves would need to break into the car physically, and hotwire it or bypass. But with relay attacks, a car can be gone in seconds.
To actually be able to capture the packets to retransmit them, the relay devices typically will need to capture the BLE advertising packets, and then be able to relay and follow the connection that the devices establish. This isn’t as difficult as it seems and there’s quite a few tools available that can perform this.
There are a few reasons Tesla and other car manufacturers use Bluetooth Low Energy. First, it’s supported in smartphones, so that you can use a smartphone as a car key. Wi-Fi wouldn’t work for a variety of reasons, and BLE is fast and low power. Low power is critical because you also want to support Keyfobs that are small and run on coin cell batteries.
Security is also built in the protocol. Using a standardized wireless protocol like Bluetooth has a lot of advantages as well such as worldwide compatibility, wide availability of parts, etc.
Detecting Proximity and Authenticating
BLE allows the vehicles to measure a the Received Signal Strength (RSSI) and latency when it’s doing challenge-response. That’s common with most wireless receivers that can give you a relative measure of signal strength (that manufacturers can then calibrate against).
However, RSSI is notoriously unreliable – if you put a device in your pocket or inside a purse, the signal will drop significantly, so a keyfob could appear to be very far when in fact it’s close. RF signals also bounce off of materials, which means you may be receiving a signal traveling longer and that’s weaker.
Because of this, RSSI data measurements are always filtered to remove outliers and try and get some more reliable data. Even with this filtering, RSSI is unreliable in determining location, and this forces car manufacturers to be more lax in deciding whether the device is near or far.
The additional challenge-response mechanism that is used by Tesla to only allow authenticated devices to unlock the car has some timing constraints placed on it, so that you’re rejected even if you’re correct but take too long to respond. But, because relay attacks can add very little latency, it’s not possible for the car to tell them apart, and relayed packets still appear to be legitimate.
One of the attacks on Tesla was developed by security researchers in which they would forward link-layer packets of two Bluetooth LE devices with as little as 8ms of latency, in a BLE connection of 30ms (minimum usually allowed by iOS) means that the relay devices are invisible.
Tesla’s Ultra-Wideband (UWB) runs into issues
Tesla has given contradicting statements on their use of UWB. In some releases, Tesla claims that it added UWB in their vehicles specifically to help stop relay attacks, as it stated in it’s 2020 filing with the FCC. A car manufacturer would rarely go through the effort and cost of adding UWB if they didn’t intend to do that.
But in other statements, Tesla says the opposite – that UWB isn’t currently being used. Tesla’s response to the security researchers was “This behavior is expected, as we are currently working on improving the reliability of UWB”.
It seems Tesla is running into issues getting UWB to mitigate relay attacks.
As expected, UWB is not a cure all for the relay attacks. Getting UWB working reliably in proximity detection can be tricky because there is always error with the system, and because smartphones and keyfobs have limitations. These errors can cause both false positives and false negatives – the car can be unlocked at longer distances than desired, or the car could reject the user that’s right next to the car.
Getting this balance right is critical and oftentimes difficult. Balance this against the relatively low probability that the car is stolen, and you can see why Tesla may have avoided enabling this unless they felt they got it right.
The good news for Tesla owners is that the hardware is in place, and Tesla could push a firmware upgrade to enable UWB to protect their cars.
References
Wired.com – Teslas Can Still Be Stolen With a Cheap Radio Hack—Despite New Keyless Tech